Blogs, Videos and Articles

This video walks through how to install and configure Graylog (v4) on FreeBSD 12.2 using binary packages. Graylog is an open source [...]

How to setup TrueNAS CORE with Windows Active Directory integration; TrueNAS CORE makes it really easy to setup Windows Active [...]

Microsoft has detected multiple 0-day exploits being used to attack on-premises versions of Microsoft Exchange Server in limited and [...]

The user records of popular VPN services have reportedly been compromised, and millions of user data are now offered for sale [...]
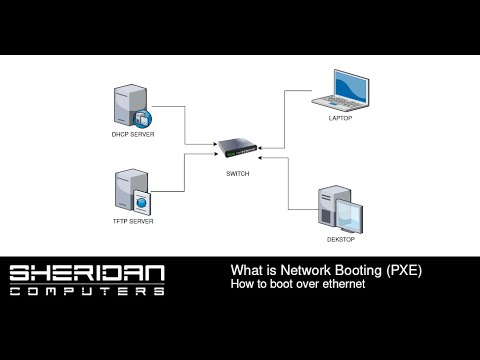
An introduction video explaining how to boot computers and laptops etc over ethernet. The ability to boot devices over a network is [...]

Microsoft (Office) 365 has many settings available to setup anti-spam policies which are probably overlooked and left unconfigured. In [...]
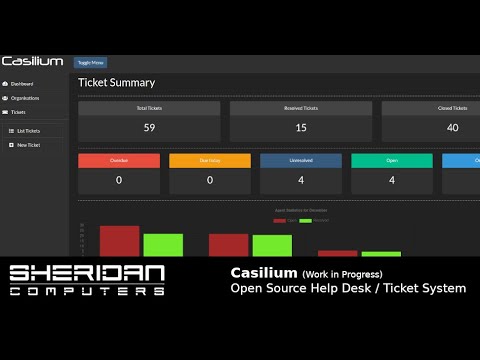
Sheridan Computers are an IT Support Company based in Manchester. As an IT Support company, or a Managed Service Provider (MSP), [...]

Unboxing of the Untangle z4 security appliance (official hardware), including basic installation and setup / overview of the prodct.

Multi-factor authentication (MFA) is an increasingly popular way to add an extra layer of security to your online accounts. With MFA, [...]

